Thanks to Whatsapp’s change in privacy policy and how it handles your personal data, a world-wide debate has started as to which IM messenger is most secure and protects your data while keeping the convenience and user-friendliness intact.
We have also covered Whatsapp’s replacement for GNU/Linux previously that works better for you. Today, we are going to talk about something different, something that is better than the rest in many ways if privacy and security of your personal data is of paramount importance to you.
Messenger from Secret Spy Agent movies
The Briar messenger focuses on anonymity and takes a completely different approach than ordinary messengers. And it has to, because Briar’s target group is political activists, journalists, etc., i.e. people who fight against or report on public grievances. The app is exclusively available for Android OS and is also available in the privacy-friendly F-Droid Store for Android in addition to the Google Play Store.
Briar does not require a central server and works with peer-to-peer network instead. It sends all messages via the Tor anonymization network out of the box, which is a great anonymity tool. This means that the metadata generated during use is disguised in such a way that it is impossible to trace who was in contact with whom. In addition, this solution is extremely resistant to censorship. Neither a telephone number nor access to the address book is required to use Briar. Although, it not an exclusive feature, because it can be configured in a similar manner on Swiss based Threema too.
Due to the meshed network option built into Briar, it can also work without a functioning Internet infrastructure and in this way support aid in disaster situations too. However, the high robustness, security and anonymity come at a price: Compared to conventional messengers, the user-friendliness is very limited and the permanent connection via the Tor network is at the expense of the battery. When you do communications over mobile platforms, battery is a major player for many end-users.
Encryption Technology
To ensure “tap-proof” communication, Briar relies on end-to-end encryption (E2EE) of message content. For once, the messenger does not use an implementation based on the Signal protocol, but a proprietary development called Bramble. Both Crypto and the Briar app itself were audited by Cure53 with the first release in 2017. They concluded as follows in their report from March 2017:
[…] For the six Cure53 testers who completed this assessment, the overall low severity translates to an application with a good understanding of vulnerability patterns and threats. […] the quality and readability of the app’s source code was rather exceptional […] Still, provided that the documented issues get fixed properly, the application is able to offer a good level of privacy and security. In other words, the Briar secure messenger can be recommended for use.
You rarely read such ratings in the final evaluation of a security audit. This speaks for Briar or the professionalism of the development team.
All messages are E2E encrypted by default, both in individual and group chat. In addition, the Briar protocol supports Perfect Forward Secrecy (PFS). However, not in every use case, as a query to the developers over IRC reads and I quote, “Briar indeed offers Perfect Forward Secrecy, but it doesn’t offer deniability for all types of communications. One-to-one messages have that security property, but one-to-many communications like groups, forums and blog posts don’t have deniability, because those messages are signed.”
Authentication
If you do not authenticate your counterpart, you can never really be sure whether you are actually exchanging messages with the desired communication partner or possibly with an unknown third party. With Briar, verification of a communication partner takes place directly at a meeting via QR code, which is then matched:
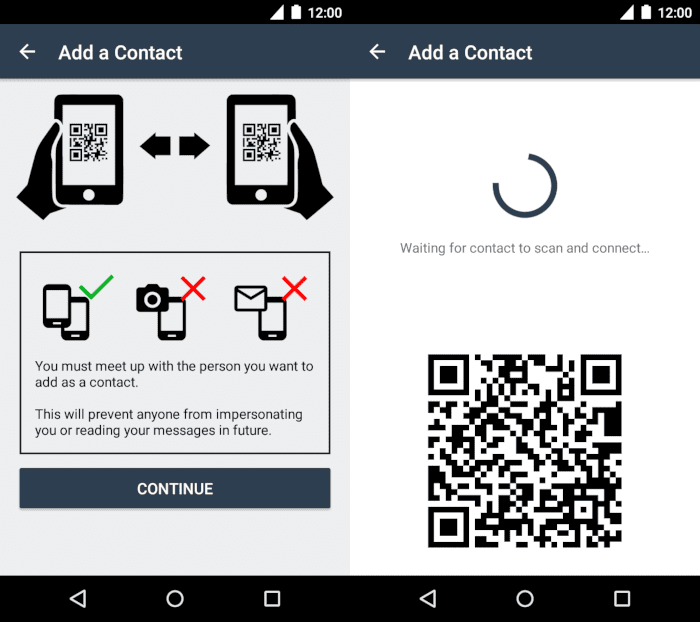
A green circle next to the contact name indicates that verification has taken place.
By the way: Contacts can also be added “remotely”, i.e. via the Internet however, verification must still take place at a real meeting.
P2P and Decentralized
Unlike most messengers, communication or message exchange does not take place via central servers, but via a peer-2-peer network. It is therefore a completely decentralized network in which messages are exchanged directly among clients without dependence on a client-server structure. This approach is extremely resistant to censorship, (almost) immune to surveillance, and hardly any metadata is generated in the process and if it is, it is additionally obfuscated via the Tor network in the case of Briar. All messages are stored exclusively on the devices of the communication partners involved.

As sensible as this approach seems, it has to contend with a few disadvantages in practice. One of them is that time-shifted communication is not possible. Users must therefore be online in order to chat with each other. Time-shifted communication, as messengers usually offer, is not possible with Briar due to the lack of a server component. The Briar developers are aware of this problem and therefore want to introduce the Briar Mailbox or repeater soon.
Briar Mailbox project aims to develop an easy way for Briar users to increase their reachability and lower the battery drain of their phone.
According to the project’s page, ‘In Briar messages are exchanged directly between contacts (peer-to-peer). This kind of synchronous message exchange requires contacts to be online and connected to each other. While this is great for privacy (no central server which can log things or be censored) it’s bad for reachability, especially in mobile networks where connectivity can be limited.’
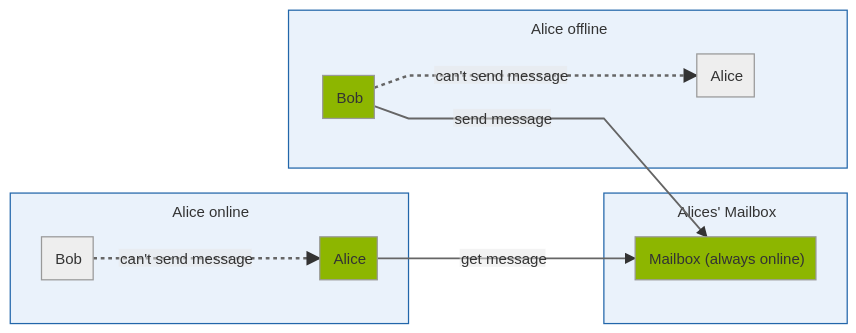
As per the project’s description, the repeater is designed to be easy to deploy with initial version or model as an Android application, so it could easily be setup on a spare phone at home connect to a reliable Internet connection without requiring a special server for it to function.
That sounds great. You practically host your own little Briar server that caches all messages and then sends them to the client. This should not only save battery power, but also reduce the problem of time-delayed communication.
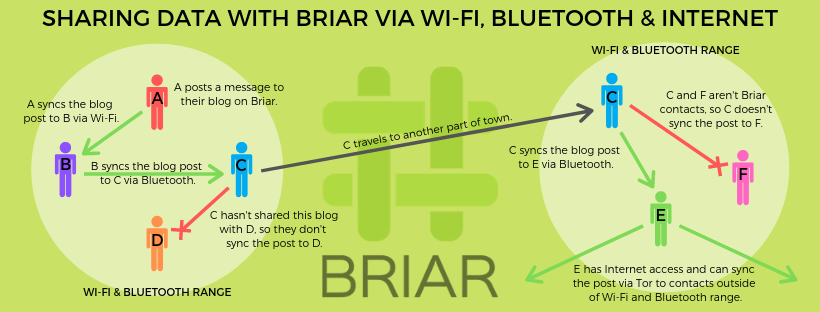
At Briar, the participants not only communicate directly with each other via the Internet, but also via WLAN and Bluetooth. So if the Internet is not available, communication is still possible. Work is also underway to enable messages to be exchanged via USB stick or SD card. But message transport via low-power wide-area networks (LPWAN/LoRa), comparable to walkies-talkies is also in the works.
Metadata
Despite an E2EE, the metadata in a messenger can still tell you quite a lot about a person:
- Who is online and when
- How many devices someone is online with
- Which contacts someone has (social graph)
- Who communicates with whom and when
- The IP addresses of the devices
So when using a centralized messenger, we have to trust the provider not to store, share or somehow exploit the metadata collected. We have somewhat more control over the metadata when using federated solutions such as XMPP or Matrix but only if the server is under our own control and if we are very good at system administration. Otherwise, the problem is similar to that of centralized services. In fact without proper knowledge of system administration, I would not recommend to you host your own things when done critical work that might pose a threat any human life.
The greatest possible avoidance of metadata collection is therefore only possible if the dependency on the server component is expunged. This is exactly what Briar does with its peer-2-peer network approach. Due to the lack of a server infrastructure and the use of the Tor network, it is practically impossible to find out who communicates with whom and when. The metadata that accumulates, such as IP address and the like, is then additionally obfuscated via the Tor network. What remains is practically only a connection to the Tor network. So you could say that Briar does not generate any metadata. This should be a great advantage, especially for activists, journalists, etc., i.e. people who fight against or report on public grievances.
With Briar, there is no central database or server that caches messages. The “trust” is therefore implemented directly in the protocol. That being so, if a communication partner is not online at the moment, the app always tries to send the respective message again.
Identifier
When you start the app for the first time, you are prompted to create an account or assign a name of your choice. Additionally, the account is secured with a password of at least 8 characters – after restarting the smartphone or if you have logged out before, you will be asked for it. This should be remembered well, because there is no option to recover it.
A classic identifier (phone number, e-mail address, etc.) is basically not available with Briar. You can choose any name for your account, the connection or assignment to another account is done via an onion address (from the Tor network). Every Briar client has its own .onion domain in the Tor network, so to speak, to which other participants or clients can send their messages. This looks like this, for example:
briar://acsvsebm2ler111oybpsgrbuwq2c6gbny4d5uicwzkbrvbzqaemgw
Two Briar users then communicate directly from device to device via the respective .onion addresses.
Unfortunately, Briar does not currently offer the option to transfer this account or the associated onion identifier to another device. So if you change your smartphone, you have to add or verify your contacts again. The Briar developers want to prevent that a Briar account exists on multiple devices at the same time and that attack vectors are opened. More information about this in this issue on their Gitlab.
Transparency and License
The source code of Briar is available under the GPLv3 license and can be viewed by everyone. Thus, an independent verification of the security is basically possible. This openness is an essential step towards more transparency of the application and thus ensures trust.
The last security audit of Briar (+Crypto) dates back to 2017, during which a few vulnerabilities were uncovered. Overall, the result was very positive. Another audit of Briar is planned after the end of the development phase.
Briar is largely funded by donations. According to the website, the project has received funding from Small Media, the Open Internet Tools Project, Access, the Open Technology Fund, the Prototype Fund, Internews, the NLnet Foundation, the Next Generation Internet programme and the ISC Project.
Features
Below are some more points worth knowing that Briar offers:
- Desktop client: a desktop client for Briar (beta) has been available since early September 2020. The installation guide describes how to get started.
- Without Google dependency: Briar can be obtained via F-Droid completely detached from the Google Play Store. But that’s not all: It also works completely without proprietary Google libraries or Firebase Cloud Messaging. By default, the client establishes a (permanent) TCP connection to the Tor network. This costs battery accordingly.
- Forums | Blogs: In addition to simple messaging between two users, Briar supports private groups, forums and blogs. In forums, any user can add other members, who then exchange messages with each other. In groups, only the group admin can do this. The blog function allows users to publish posts, which are then transmitted to all contacts.
- RSS reader: Briar allows you to subscribe or read RSS feeds. The articles are downloaded over the Tor network to protect privacy.
- WLAN | Bluetooth: If users are in close proximity to each other, Briar can also send messages via WLAN or Bluetooth. It will soon be possible to exchange messages via low-power wide-area networks (LPWAN/LoRa).
Briar: pros and cons at a glance
Positives:
- The client is open source and the source code can thus be viewed
- By default, end-to-end encryption is active for chats and also private group chats
- Briar can be used without linking a phone number – identifier is a .onion domain
- Can also be used on Google-free smartphones
- Does not use the Google infrastructure for push notifications
- No (user) trackers integrated
- No dependence on central servers
- Extremely robust, censorship resistant and high protection against surveillance
- No storage or collection of metadata / messages
Negative:
- Only suitable for chatting (no pictures, videos, etc.)
- No backup option (e.g. when moving to a new smartphone) – see also: How do I backup my account?
- No time-shifted communication possible
- Increased battery consumption
- No iOS version (and until the Briar Mailbox is implemented, it probably won’t be) – see also: Will there be an iOS version of Briar?
I wish, Briar did not have these negatives at all. But there is always a balance between convenience and anonymity/security. While some of the above issues can be resolved with resources and time but Briar would never be WhatsApp-like in terms of user-friendly or feature list.
Conclusion
The focus of Briar is clearly on security, anonymity and an innovative way of messaging. Due to the associated restrictions, Briar’s target group is not the average user, but (political) activists, journalists etc. Even in the default settings, Briar achieves a high level of protection. If activists were to organize themselves via it, they would have a robust, censorship-resistant messenger that makes control or monitoring difficult to impossible. The nightmare of dictators and states that maintain their power with repressive measures and censorship.
Briar is genuine P2P, E2E messenger without any metadata collection that uses Tor like Anonymity tool to communicate over Internet when required by default. This model if properly deployed and audited is robust against oppressive regimes and any Internet surveillance. If you are doing anything serious or critical, go for it. No email, no phone number, no IP addresses, no centralized server, no plain-text. Just pure encryption and transport obfuscation. It is authentic privacy by design. Period.









