Introduction
Owning a popular Android phone comes with an itch to customize it fully if you happen to be a tech-savvy user or a pro user. We are not talking about custom external skins/cases here. We are talking about replacing the mobile OS that the phone ships with something that we like that may or may not talk to Google’s servers any more. These Google’s Android based alternative OS or full ROMs on Android phones have a huge community and support system, it is a growing a thriving business too. The craze of using custom ROMs is so high that people flash their brand new smartphones with third party ROMs without worrying about voiding their warranties.
For last couple of years, we all have relied on custom Android ROMs for variable reasons from extending phone’s life with latest Android versions and some for privacy/security reasons to not use Google Apps on your smartphone. One such name in the realm is LineageOS once called Cyanogenmod, which has been tried by most of us. It made it unavoidable for a lot of pro users to not try it once for above said reasons.
LineageOS with a few efforts meet the privacy requirements of most users. However, security is a different case. It isn’t even the fault of LineageOS Android distribution, it is the OEMs, who fail to provide timely firmware and kernel updates. Which is why we must think thrice before being an expensive Android device. The manufacturer or cellphone company must have a good track record for the same.
If you care for Android security, it is time to introduce you to security-centric and privacy focused Google-free Android distribution called CopperheadOS from a privacy focused Canadian company called Copperhead. It is a Toronto, Ontario, Canada based Cyber Security firm and a professional team of Mobile security specialists. It sets high standards in security and data protection.

Sadly, even CopperheadOS cannot help with the problem of some hardware/chip related support times. That is still in the hands of the device or chip manufacturers like Qualcomm. However, the devices officially supported by CopperheadOS (Google Pixel series) are supplied with persistent security updates for at least three years. CopperheadOS currently supported on the Pixel 2, Pixel 3, Pixel 3a, Pixel 4 and Pixel 4a series. Pixel 2 series being the oldest supported devices originally announced in Oct of 2017. This means that there is currently no long-term solution for the update problem. However, those who have the highest demands on security and data protection will not be able to avoid CopperheadOS – as long as Android is the preferred platform. It comes with a plethora of security hardening and enhancements in every stratum of Android OS. When you use CopperheadOS, you expect nothing but state-of-the-art security by default.
“Copperhead is the trusted choice of intelligence agencies, militaries, Fortune 500 companies and NGOs worldwide. Get the world’s most secure OS on the world’s most secure device.“
It gives you precise control of your digital life. You get protection from zero-days and related exploits, absolutely no Google or any other tracking analytics.

There is verified boot, locked bootloader, hardened kernel, advanced sandboxing and application isolation too. Overall as an end-user, you get untraceable, self-contained, secure and private experience from your Pixel device running CopperheadOS.
CopperheadOS
CopperheadOS is open to audit and has its source-code available under the Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International license, along with some portions that are GPL2 (kernel) or GPL3 (F-Droid). Until recently it was completely gratis for personal use. Albeit for commercial or business use of part or all source-code of Copperhead’s Android distribution, you are required to have a license to do so from Copperhead, it comes with a lot of benefits too as per Mr James Donaldson at Copperhead. Moreover, non-profits are offered exemption from commercial use provided that required documents are furnished. It is a nice model to distribute open code to commercial / business bodies and entities while keeping the source-code open for public to audit, review and for other educational purposes.
The focus of CopperheadOS is on improving Android’s privacy and security. For this reason, the project does not include any Google Apps, Services or even its free/open implementations of Google’s proprietary Android Apps and libraries like microG. As it brings insecure code-base and more attack surface. All components that are not required for Android base compatibility are not integrated. Copperhead is based on the Android Open Source Project (AOSP), but extends it with functions and measures that improve security and data protection.
Commercial Availability and Limited Device support
I hope you do not expect a robust Android distribution like CopperheadOS to be made available for gratis. When you are not paying for the product, you are the product. CopperheadOS was made available as a paid product ever with the launch of the Pixel support and its development in March 2017. Since the launch of Pixel support, users could either buy a phone from the Copperhead store with CopperheadOS pre-loaded, or send their own phone to Copperhead for the operating system to be installed on it.
Copperhead offered directly flash-able builds of CopperheadOS for Nexus devices viz. Nexus 5 and 6p between 2016 to 2018. But owing to rampant abuse and violation of previous permissive license mostly by other commercial companies and entities, it had to change the license of its source-code. It was a calculated decision to sustain the whole project and pay for much needed resources owing to limited budget at hand. If there would be no CopperheadOS, no secure, privacy-aware Android distribution for those who actually need it or for non-profit doing seriously critical social work that require mobile OPSEC. In the end if the project discontinues, no one would benefit from it. I personally support this change by CEO of Copperhead. Also, I believe, people should start to learn to pay for digital or intangible products now especially for commercial or business use. If not, there would be no big and small companies like Copperhead offering legit, robust, privacy-first solutions any more.
Currently, you can get a CopperheadOS via Copperhead Partner network via hardware and software downloads. It is available at a much reasonable price.
CopperheadOS only supports Google Pixel devices that have an attestation for alternative operating systems and support Verified Boot. In view of the project’s clear focus on security and data protection, only Pixel devices that are supplied with (security) updates by Google for at least three years are supported. A justification for their selection can be found in official minimum requirements for CopperheadOS support. It is hard to find such quality hardware in realm of Android smartphones as of yet. You have to keep in mind that this Android distribution or ROM do not cut corners and want the best privacy and security options out there or top of the line security as Copperhead claims.
It is logically untenable that you have to buy a Google device for the best possible security and data protection in Android world. You are forced to support the very company that violates the privacy of its customers massively and permanently. Therefore, CopperheadOS might not be an option for everyone.
The strict minimum requirements of CopperheadOS for the security of the devices might be the sticking point, which is why many devices are out of the question from the start. Thus, those who want to use it have to swallow the “bitter pill” and invest in a Google Pixel device once in 3 years [unless Google extends its device update and support policies beyond 3 years].
Security and Hardening
CopperheadOS only uses devices that support Verified Boot and many other good things as per the technical overview. This is to ensure that all executed code comes from a trusted source and that an attacker has not tampered with it. Among other things, this is intended to detect Evil Maid attacks, where an attacker has access to the device. If a device has an open bootloader (unlocked) and/or a recovery image has also been installed, it is possible for a skilled attacker to make changes that the user does not recognize afterwards. The Android device encryption, which is also queried when booting into the recovery, only protects the user data. However, an attacker can still access the system partition via ADB (Android Debug Bridge) and make changes. A change of the bootloader is also conceivable. Admittedly, this is a rather low risk, but the possibility still exists. It only boots when no (manipulative) changes by a third party to the boot loader, system, vendor files, etc. have been detected.
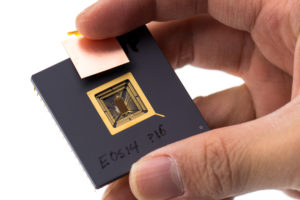
Google Pixel devices also feature the Titan M chip, which brings the following security improvements, among others:
a. Storage of biometric features (fingerprint, face) directly in the chip, without the possibility of extracting them from there.
b. Interaction with Verified Boot to ensure that there is no tampering with the device
c. Improved brute force protection to prevent an attacker from making any number of attempts at unlocking the device
d. Via Android API, private keys or passwords from apps can be securely stored directly in Titan-M
Apart from the above said hardware security measures that Pixel devices already come with out of the box, CopperheadOS itself refines the system’s security. This includes hardening measures on the kernel, the libc library, and a malloc proprietary development that is supposed to provide protection against heap corruption vulnerabilities. CopperheadOS replaces the system allocator with a hardened malloc implementation.
According to Copperhead, default settings have been altered to emphasize privacy over small conveniences. For instance, Location tagging is disabled by default in the Camera app. Personalized keyboard suggestions based on gathering input history are disabled by default. Sensitive notifications are hidden on the lockscreen by default. Passwords are hidden by default. These might seem trivial but it is of grave importance in operational security.
The included security-focused apps have a lot of additional enchancements. CopperheadOS ships a custom build of Android’s WebView along with a standalone build of Chromium from the same source tree. Unlike Google’s Chrome app, the CopperheadOS Chromium app is 64-bit. Chromium supports per-site-instance sandboxing. Using Chromium or a WebView-based browser has the advantage of reducing attack surface compared to another browser engine. DuckDuckGo has been added as a search engine option and is set as the default. CopperheadOS also disables the Location permission group for the browser by default since Chromium knows how to request it when needed and many users don’t use it.
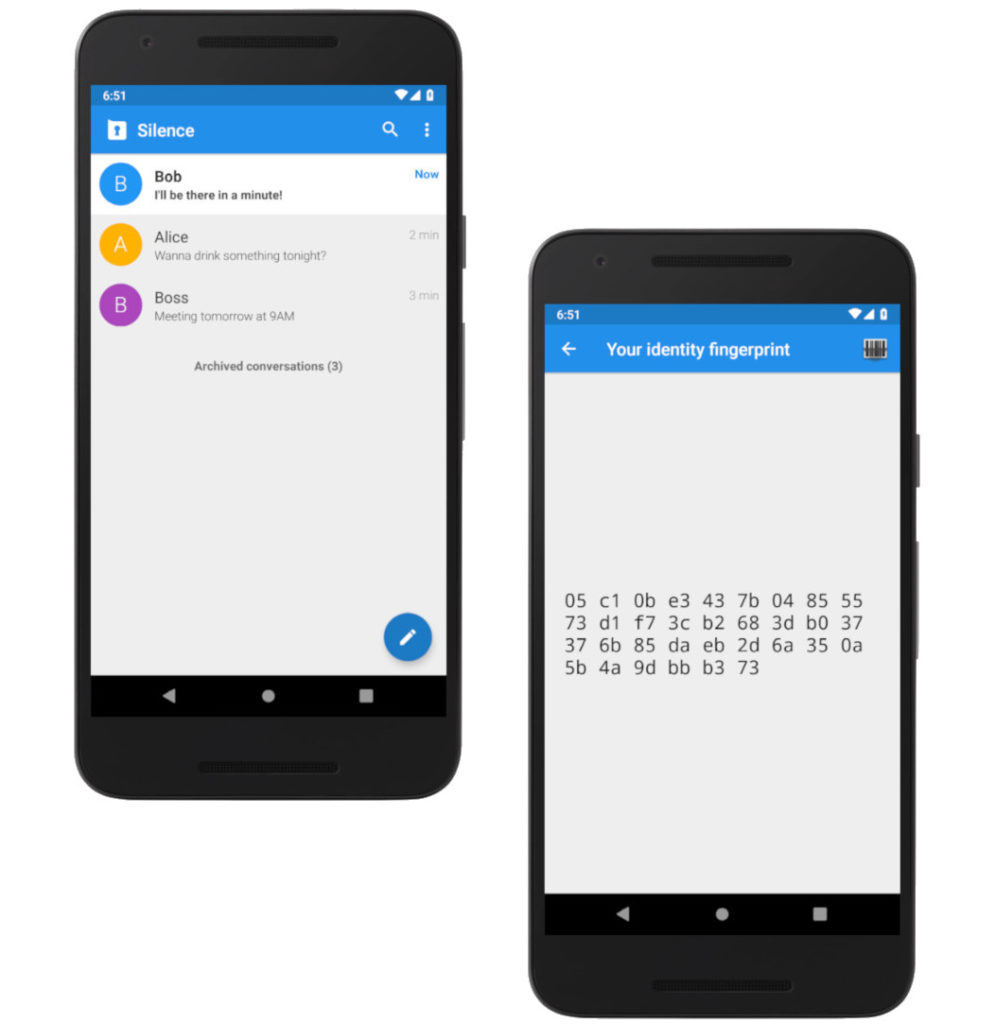
The AOSP SMS app (Messaging) is replaced with Silence to provide the option of end-to-end encryption over SMS when a data connection is not available to either contact to enable better options.
CopperheadOS includes a custom PDF Viewer based on pdf.js in a WebView. It doesn’t require any permissions since it relies on content providers via ACTION_VIEW and ACTION_OPEN_DOCUMENT for the application/pdf mime type rather than requesting storage access. It only has access to data that the user explicitly provides to it.
Some AOSP apps like calendar are replaced with free and open security focused apps like Etar to offer better privacy equation.
Seedvault, an encrypted backup and restore application, is integrated into CopperheadOS to provide users with a seamless backup/restore process.
Another measure that not only increases security, but also protects privacy in particular, is not using Google services or apps within CopperheadOS. This additionally ensures a reduced attack surface.
Baseband isolation
In addition to the aforementioned security measures, Google Pixel devices or CopperheadOS isolate the mobile and WiFi baseband from the system via an IOMMU. Memory access is partitioned by the IOMMU and restricted to the internal memory and the memory shared by the driver implementations. Because of the separation or isolation, an attacker has to overcome an additional hurdle to access the operating system (e.g. via kernel userspace).
Default Data Sending behaviour
A feature of modern systems like Windows 10 is the collection and processing of telemetry and diagnostic data. In a privacy-oriented system, on the other hand, one expects an absolute minimum of data transmissions. CopperheadOS comes very close to this idea, but with small restrictions. In the usage guide, the sub-section, “Default connections made by CopperheadOS”, transparently lists all connections that the system or included apps establish, which is as follows:
- The CopperheadOS Updater app fetches update metadata from https://SERVER/DEVICE-CHANNEL every hour when connected to a permitted network for updates.
- F-Droid performs update checks for enabled repositories. By default, the standard F-Droid repository is enabled.
- As with other devices with a Qualcomm baseband (which provides GPS), GPS almanac updates from Qualcomm are downloaded from https://xtrapath1.izatcloud.net/xtra3grc.bin, https://xtrapath2.izatcloud.net/xtra3grc.bin or https://xtrapath3.izatcloud.net/xtra3grc.bin. CopperheadOS has modified all references to these servers to use HTTPS rather than a mix of HTTP and HTTPS.
- Connectivity checks designed to mimic a web browser user agent are performed by using HTTP and HTTPS to fetch standard URLs generating an HTTP 204 status code. This is used to detect when internet connectivity is lost on a network, which triggers fallback to other available networks if possible. These checks are designed to detect and handle captive portals which substitute the expected empty 204 response with their own web page. These need use a very common domain and URL in order to bypass whitelisting systems only permitting access to common domains / URLs so a domain like copperhead.co would be inadequate.
- CopperheadOS leaves these set to the standard four URLs to blend into the crowd of billions of other Android devices with and without Google Mobile Services performing the same empty GET requests:
- HTTPS: https://www.google.com/generate\_204
- HTTP: http://connectivitycheck.gstatic.com/generate\_204
- HTTP fallback: http://www.google.com/gen\_204
- HTTP other fallback: http://play.googleapis.com/generate\_204
- DNS connectivity and functionality tests
- DNS resolution for other connections
The connectivity checks are performed by both the OS itself and the hardened Chromium browser.
As per the usage guide, ‘Unlike stock Android, CopperheadOS uses Cloudflare’s DNS servers for network connectivity tests and the default fallback when the network doesn’t provide DNS servers. This decision is based on Cloudflare providing a stellar privacy policy compared to the decent one for Google Public DNS.’
Conclusion
As you read above, CopperheadOS is the best Android distribution when it comes to privacy and security. If Google Pixel devices is something you can afford, you better get in touch Copperhead team and/or their official partners to obtain a device or installation for yourself. You should not wait another second and take control of your digital life again. Privacy is something worth paying for. It is about time, we learn to appreciate the tireless hard work and efforts by developers and various teams in projects like CopperheadOS to bring out the best in terms of Android security and privacy for all users.
That being so, it is not for all, if you are a student you cannot afford it as of yet. Keep studying it. Talk about it. It has a lot of educational value as a young developer or coder. It is not expensive, remember how Apple’s pro stand was later justified as it was still a better deal versus other OEMs over all including the monitor.
The only issue, I see which would be covered in upcoming posts is Apps those require Google Apps or libraries to function. Also, lack of inclusion of microG like replacement can be irksome for a few users. I believe with no root access and properly locked bootloader, most of the apps including finance related or bank apps should function just fine.
I get my apps mainly from the F-Droid store including email, chat, video, games etc. You should give up or forget about Google Play Store for obvious reasonable App publishers do offer APKs directly on the website too. But owing to the dominance of Google’s Android market, you might find a FOSS client to Google’s Play Store called Aurora Store useful to get and update your favourite apps if they don’t have a F-droid repo yet.
But you will be in a legal gray area, so per a sub-section of usage guide of CopperheadOS, it is not recommended to use your own Google Account or credentials as of yet. Most of the paid apps deploy DRM and won’t work without Google Apps anyway.
You are also going to love the frequent updates that you will receive from Copperhead. Also, CopperheadOS has a unique way to alert you or notify you during a system update with a continuous notification sound until the update is complete. CopperheadOS will bring you visual changes and more improvements over the time other than fixes and patches. You should check out their change logs to know more.
Lastly, having known good amount of details about CopperheadOS, I can affirm, if security and privacy is your end goal, Google-free Android distribution like CopperheadOS with robust business / commercial support, easy licensing options should be your first and last stop. Period.







This was an extremely well written and informative article. Thank you for all the information it will help out in the future.
Love it and love CopperheadOS! Do you know how to buy it?
You need to get in touch with them directly over web https://copperhead.co/contact/ or Telegram via https://t.me/copperheads
CopperheadOS is an expensive rip-off. If you support open source don’t support CopperheadOS they’re anti open source and a massive fraud. Look up GrapheneOS, it’s the free(as in free beer) and open source OS CopperheadOS is forking from. Check out Grapheneos.org site, even documentation are copied by CopperheadOS. Even the Twitter CEO endorse GrapheneOS: https://mobile.twitter.com/jack/status/1355295732836626432