ODoH
DNS is like a universal phone diary or address book of the Internet. It is very basic definition of how we resolve a website or a webpage online. It may come across as trivial but it is a complex task to secure it. We cannot rule out the fact that lack of built-in security and basic privacy can cause serious misconduct of metadata that is being collect universally by all the all the ISPs and government, let alone intelligence bodies around the globe.
In other to prevent such misconduct, instead of making cleartext queries over default port 53 (UDP), it is performed over TLS or HTTPS in an encrypted manner using protocols like DNS over TLS (DoT) or DNS over HTTPS (DoH). Although, both of these encrypted DNS protocols are fine with a few caveats. These are IETF standardized protocols for DNS encryption that eliminates opportunities for eavesdropping and on-path tampering with DNS queries.
Thanks to revelations by Edward Snowden, we saw wide-spread adoption of encryption tools and the tech giants also had to cave in to popular demand by its users and critics. Google’s Android and iOS, the popular mobile OSes also baked it into their respective OS.
DoH has gained much more traction as popular open-source browsers like Firefox has introduced it as built-in privacy tool. It mattered a lot because it is the first time a web browser used by masses introduced something useful by default for its users. Last year, Firefox was in news for sending millions of encrypted DNS queries to one or two trusted DNS resolvers by default. Despite public uproar, they still continue to do so by default in the US. Google Chrome followed Firefox and deployed DNS-over-HTTPS or secure DNS for its users in May of 2020.
Even though DoH is good as it protects the integrity and privacy of your DNS queries by encrypting them but your trusted DNS resolvers still have your IP address and DNS query both. It is linkable metadata. It is a matter of grave privacy concern. Any DNS resolver like Cloudflare, Google, Quad9 could technically retain the data if they wanted to. It is just a privacy by policy. Unless we have privacy by design with properly implemented mathematics and open code available for public audit, can we really reckon on these DNS encryption standards? I guess not.
In order to address this privacy and security issue directly related to sensitive DNS queries and IP addresses, a team of concerned engineers from Cloudflare, Apple, and Fastly worked together on a DNS standard, which is essentially an extension to DoH to hide client’s IP addresses via a proxy that handles the encrypted DNS transactions. According to Cloudflare’s announcement via a blog post they have made the source code available, for you to try or run our own ODoH service / resolver if we wanted to.
How do they do it?
There are three major players in ODoH path, viz. client, proxy and the target.
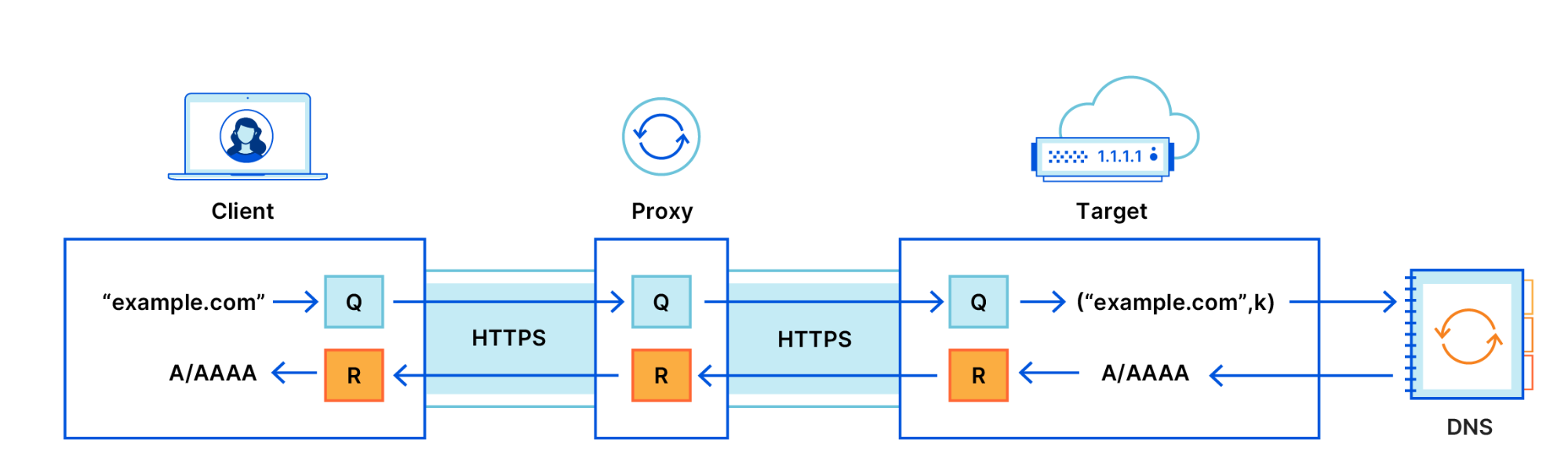
If you see the above figure by Cloudflare, it explains how a client makes an encrypted query via a proxy to the target, which decrypts the queries encrypted by the client to encrypt the responses in order to return them to the proxy for the client. Basically, how it works is, the target never get to see client’s IP as it sees the query and the proxy’s IP. Whereas the proxy never sees the encrypted DNS queries or responses as only the target get to decrypt / encrypt them for the client via a proxy.
ODoH is an emerging protocol being developed at the IETF. ODoH works by adding a layer of public key encryption, as well as a network proxy between clients and DoH servers such as 1.1.1.1. The combination of these two added elements guarantees that only the user has access to both the DNS messages and their own IP address at the same time.
This is how ODoH work to protect security, privacy and integrity of DNS queries. The ODoH protocol provides privacy guarantees when the oblivious target/resolver and the oblivious proxy operate as independent bodies and do not collude. I would like some trusted tech related non-profits run such proxies with public donations.

Today, Cloudflare is working with various ODoH proxy partners including PCCW, SURF, and Equinix.
Is it pro censorship?
Not necessarily for greater good, as this newly proposed DNS protocol grants a software publisher an easy method to deploy censorship without having to reveal the identify of users by using a ODoH proxy run by a trusted body or party or non-profit with a target/resolver that censors all the DNS requests stated by anyone including an oppressive regime. It might bring relief to ISPs who are ordered to censor certain things by Government or Law for instance adult or anti-social content. One important question we all need to ask ourselves is whether ODoH promoting anonymous censorship. Was it the real motto behind development of this protocol?
Also, how different is it from using encrypted DNS protocols like DoT,DoH or DNScrypt over Tor? I believe if user identity is a concern, Tor like networks as a proxy is a better choice instead.
Nevertheless, any development towards improvement of existing encryption DNS implementations or technologies at IETF cannot go in vain. It is a good concept on paper, if not the most ideal one. Further, the fact that it can easily be implemented right your web browser without having to run additional DNS proxies and clients on the system or OS gives ODoH a great mileage like DoH. I hope it gets wide-spread ethical implementation and adoption as expected by all.
Dog, the command-line DNS client
We all have been using nslookup and dig on Windows and GNU+Linux respectively for many years. Both of the above said binaries have been helping us resolve DNS queries including various DNS record types.
dog is an open-source DNS client for the command-line. It has colorful output, supports the DoT and DoH protocols, and can emit JSON. Although, it is a command-line software but it is pretty with output.
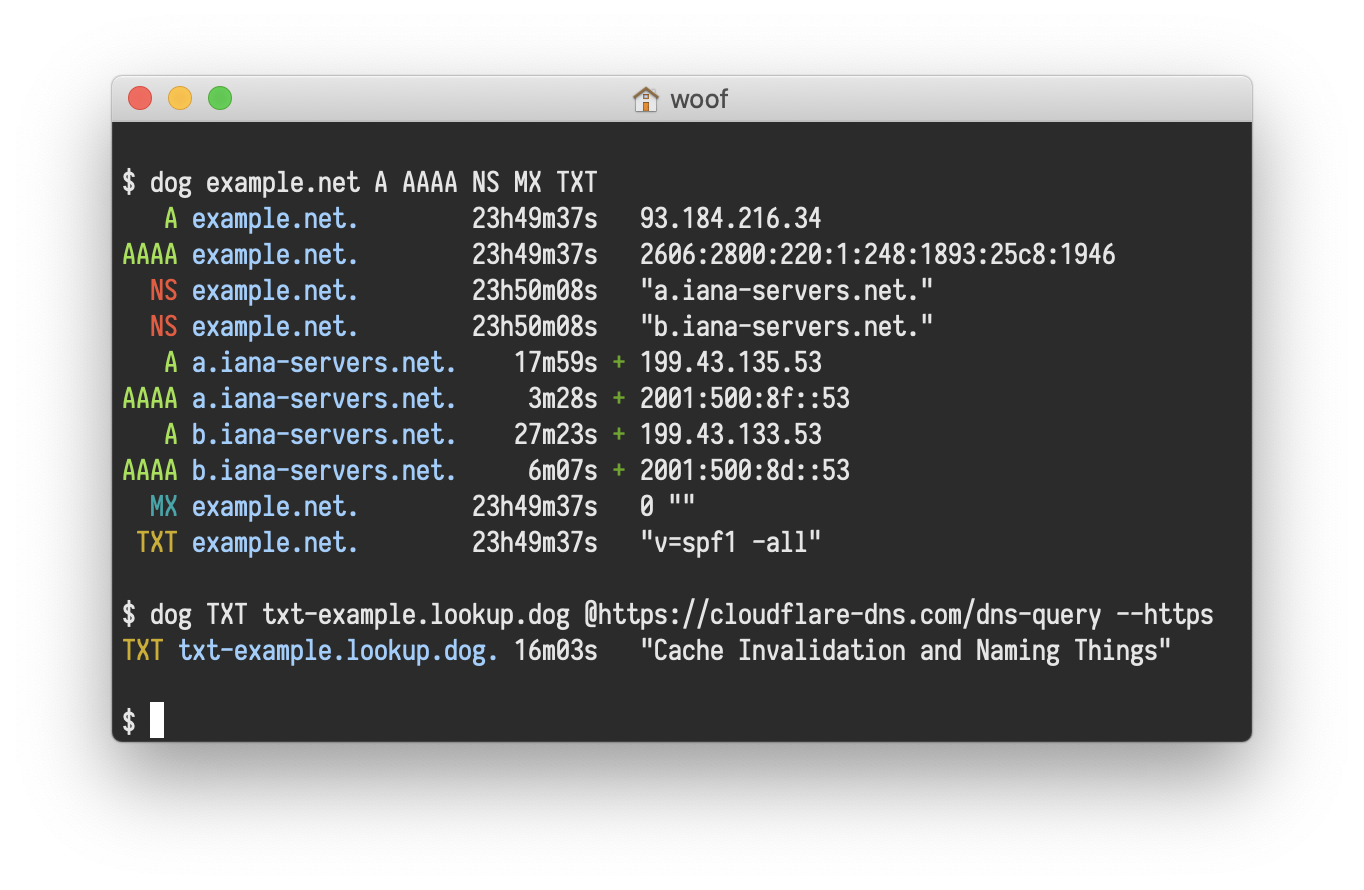
Easy to use, install pre-compiled binaries are available for Windows, macOS and GNU/Linux. Package is available for Arch Linux to install directly from the repo. Of course, It’s free, open-source and available under European Union Public License 1.2 with source-code available at Github.
Features
Sending queries and various options
By default, dog request ‘A records’ when you pass in the domain you want to query as an argument.
Record types
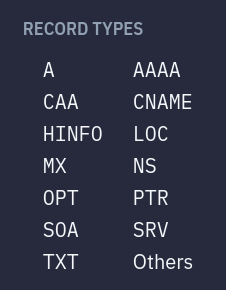
You can request all the record types such as MX, PTR, SRV, CAA etc.
$ dog example.com MX
Nameservers
You can specify which DNS server the request should be sent as follows:
$ dog example.com @9.9.9.9
It supports encrypted DNS protocols like DoH and DoT to prevent tampering of DNS queries and responses.
To send queries over TLS, pass the -T or –tls command-line option.
$ dog example.com --tls @dns.google
To send queries over HTTPS, pass the -H or –https command-line option.
$ dog example.com --https @https://dns.njal.la/dns-query
By using the same port and protocol as the HTTPS traffic used for the Web, DNS traffic can blend in, and avoid being detected or blocked.
Classes
The DNS protocol actually has support for different classes of networked computers. By default, DNS requests are queried with the IN (Internet) class, but there’s also CH (Chaosnet), an early network, and HS (Hesiod), an alternate naming system.
To use any of these three, pass them as command-line arguments. There are no record types called IN, HS, or CH, so this is unambiguous.
$ dog example.com CH
UDP, TCP and Automatic protocol switching
Dog sends a query over UDP, it is the default behavior it exhibits.
To send packets over TCP, instead of UDP, pass the -T or –tcp command-line options.
$ dog example.com –tcp
Automatic Switching
As most of you know already, one of the negatives when using UDP is that its packets are limited to 4,096 bytes. This is not usually a problem, as a normal response to a DNS query will be hundreds of bytes at most. However, large responses, such as those containing multiple DNSSEC keys, will reach the limit and will not be able to be sent over UDP.
By default, dog will detect if this is happening — a DNS server will send an error response indicating the payload is too large — and will automatically re-send the query using TCP if it’s too big for UDP. We all know dog as a loyal and intelligent pet but now you know it can handle DNS intelligently too.
However, you can always override this by explicitly passing the -U or –udp command-line option.
JSON output
dog can format its output as JSON. If it is being run as part of a script, of if the results are going to be sent to another program, it is preferable to output in a machine-readable language instead of attempting to parse the default output, which is meant to be read by people.
To output as JSON, pass the -J or –json command-line option.
$ dog example.com A AAAA MX TXT --json
The results will be in a top-level object, and each response will contain the original query, as well as the Answer, Additional, and Authoritative sections.
The JSON produced will be unformatted, with no whitespace or line breaks. To make it more readable for a person, pipe it through a JSON formatter such as jq.
$ dog example.com --json | jq
{
"responses": [
{
"additionals": [],
"answers": [
{
"address": "93.184.216.34",
"class": "IN",
"name": "example.com.",
"ttl": 648,
"type": "A"
}
],
"authorities": [],
"queries": [
{
"class": "IN",
"name": "example.com.",
"type": 1
}
]
}
]
}
Short Mode
A common thing to want to do is to get one answer from one query, skipping the TTLs and Additional and Authoritative sections of the response.
In short mode, dog will do just that. Running dog in short mode does one of two things:
- If the response is received successfully, and there is more than one record in the Answer section, dog will print just the values to standard output, and return 0.
- If there is an error, or no records in the Answer section, dog will print the error to standard error, and return a non-zero exit status.
To run dog in short mode, pass the -1 or –short command-line option.
$ dog dns.google -1 8.8.8.8 8.8.4.4 [Exit status 0]
To conclude, dog is a beautiful command-line dns client that does all the DNS query magic intelligently. It is security and privacy aware without of the box with support for DNS over TLS/HTTPS. Also, automatic protocol switching from UDP to TCP while doing complex/lengthy DNS query says a lot about the amount of thought put in the code. JSON output makes it a lot easy for coders or developers to process the output of DNS queries. I hope as it matures, we get out of the box support for ODoH and more fun and colorful options to play with. DNS is the backbone of Internet and having more user-friendly tools that support encrypted transactions with it is a net win for all.









