This post explains in detail how you can secure your computer straight from the startup. By securing your BIOS not only you will be able to prevent your computer from malicious programs but also from other users who wish to steal information or damage your data.
This is a guest post by Brianne Walter. Brianne is a blogger by profession. She loves writing on technology and luxury. Beside this she is fond of gadgets. Recently an article on Dell Inspiron 15r i5 attracted her attention. These days she is busy in writing an article on gaming chairs. If you would like to write a guest post for us, have a look at this page.
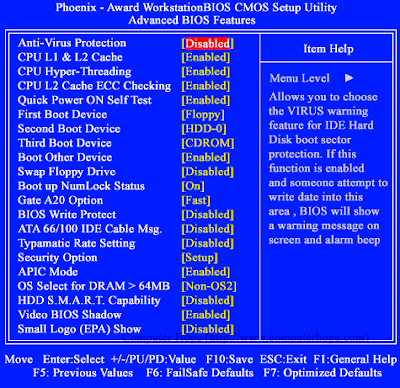 |
| BIOS Setup Screen |
The word BIOS stands for “Basic Input/output System”. The BIOS is an in-built software function that is responsible for the determination of the tasks the computer is about to perform without any access of the programs from the disk. In personal computers, the BIOS system possesses the code to regulate the display screen, keyboard, serial communications and similar other miscellaneous functions.
The BIOS is generally located on the ROM chip that is available with the computer. This is actually why it is often termed as the ROM BIOS. The reason behind this is to ensure the availability of the BIOS irrespective of any kind of failure in the system. Thus the BIOS is an easy access at any point of time and hence is generally not damaged by any kind of failure in the disk.
Today’s computer offers a varied security features with the provision to secure the BIOS in a more advanced way. However, inexperienced novice users must not lay their hands to make any changes in the BIOS settings. The following briefly states 3 steps to secure the BIOS of a computer.
Step one: BIOS Password Protection
Majority of the BIOS versions usually used today support the activation of password protection. This feature should be opted as a last resort only, if none other ways of protection to the BIOS is available. While activating the password protection it should be decided beforehand whether the password should restrict a user to access only the BIOS or the computer as a whole. In certain cases, there might be specific different password for the different checks. It is to be noted that enabling administrator’s password to the BIOS restricts any unauthorized access to the computer and thus the chances of corrupting the BIOS reduces readily.
Step two: Setting the Boot Sequence
Boot sequence is the order by which the computer boots during start up. The sequence should be in such a manner that the computer boots from the operating system in the hard disk at first and then proceeds to the other drives. This is the only convenient way to keep the system safe and secured from virus and other third party threats. Besides, maintaining such a sequence effectively reduces wastage in time and keeps the system secured from excess wear and tear.
Step three: Turning off Bootable USB devices
The third step is to turn off the provision to boot from any external USB devices. If this setting is turned on, there is always a provision to boot the system directly using any kind of external devices to the computer. In a way the risk of BIOS infiltration gets very high. Any user can manipulate the settings if this feature is turned on in the BIOS setting of the respective computer.
It is always better to leave the BIOS in the hands of a skilled technician. Normal users accessing computer on a daily basis lacks the proper knowledge of BIOS system manipulation. Hence the chances of system corrupt increases if any sudden changes are made to the BIOS. Though it is true to secure the BIOS to restrict third party interference and infiltration, improper manipulation might result to adverse results and corrupt the BIOS mechanism which ultimately ends up damaging the computer.
—Saurav Modak
Each post takes two days or more of research and three hours of typing to bring out the high quality you see here. If you admire our efforts, consider Liking Us in Facebook. Subscribe to our RSS Feeds, to get alerts of new posts. You can also Follow Me on Twitter.